Ransomware is malicious malware that obstructs users from accessing their devices or encrypts a user’s files until the ransom is paid.
There are different variations of ransomware; some variants are designed to attack Windows PCs while other versions infect Macs or mobile devices. Ransomware has become highly effective because of the sophisticated encryption or locking of the files are nearly impossible to decrypt without paying the ransom.
History of Ransomware
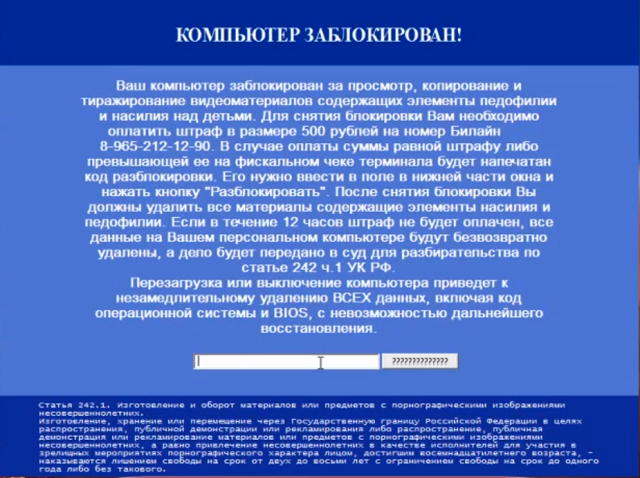
Ransomware has been the most prevalent cyber threat for over a decade. The first ransomware specimens were discovered in Russia between 2005 and 2006. These forms of ransomware were created by Russian organized criminals, and were largely aimed at Russian victims but also included those living in neighboring countries such as Ukraine and Kazakhstan. Below, we can see the first ransom note discovered from a variant named TROJ_CRYZIP.A. This form of ransomware affected machines running Windows 98, ME, NT, 2000, XP, and Server 2003. Like most forms of ransomware today, the malware targeted and encrypted certain types of files, moved them to a password-protected ZIP folder and demanded a ransom. In 2006, the ransom was paid to an E-Gold account which is the predecessor to Bitcoin wallets which is used today.
Between 2006 and 2013, two distinct varieties of ransomware which remain consistent developed: crypto and locker based. Crypto-ransomware are ransomware variants that actually encrypt files and folders, hard drives, etc. Crypto-Locker ransomware only locks users out of their devices, most often seen with Android devices.
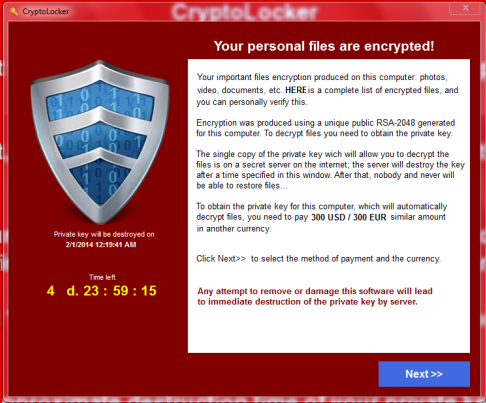
Towards the end of 2013, the first widely-recognizable crypto-ransomware appeared; CryptoLocker. CryptoLocker is a type of ransomware that renders your entire computer unusable by encrypting all your files. Once the encryption process has completed, a ransom note like the one below will appear, demanding a monetary payment for the decryption key. Like many variants of ransomware we see today, CryptoLocker was distributed through infected email attachments, which were spread via mass spam networks. Once infected, victims would have 72 hours to pay the ransom until their encrypted files would be deleted forever. In the first year alone, the creators of CryptoLocker received $27 million in ransom payments.
Since the emergence of CrypoLocker, tens of thousands of variants of ransomware have appeared. The ransomware market has become so lucrative that cybercriminals are making careers out of it. 2016, tabbed as the ‘Year of Ransomware’ saw ransomware attacks increase by 500% over 2015. On average, 30,000 to 35,000 devices were infected in 2016, with over $1 billion in ransom payments for the year. Furthermore, the number of variants that appeared per month in 2016 rose 600% with an average of 50 new ransomware variants appearing per month.
The Future of Ransomware
Ransomware isn’t going anywhere. In fact, ransomware attacks are expected to double over the number of attacks in 2016. More than 50% of businesses are projected to be hit with ransomware sometime in 2017. Of the 50% hit, less than 40% of businesses will recover all their encrypted files, whether that be from paying the ransom or from initiating their backup. Cybercriminals are just making too much money in a short amount of time to stop distributing ransomware.
Based on what we have seen in the first two months of 2017, we expect Ransomware-as-a-Service to gain more popularity. Ransomware-as-a-service (RaaS) allows cybercriminals of all technical abilities to easily distribute the malware. Creators of the ransomware charge anywhere between 5%-25% of ransom payments while the distributors receive the remaining ransom.
